Nist Csf Policy Templates
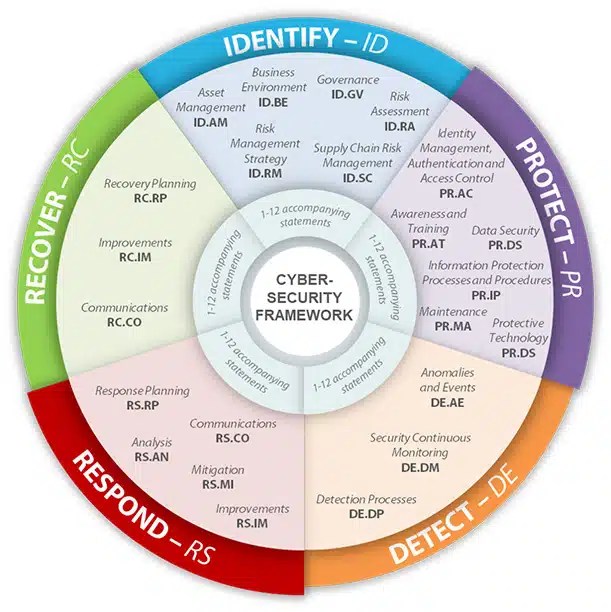
Nist Csf Policy Templates - Nist ir 8374 reflects changes made to the. 6 functions of nist csf 2.0 framework the nist csf framework has 6 core functions which help organizations to strengthen their security posture. Implementing policies closely aligned nist cybersecurity framework (csf) 2.0 enables organizations to adhere cybersecurity best practices in a flexible matter, which can be. This guide gives the correlation between 49 of the nist csf subcategories, and applicable policy and standard templates. View the quick start guides. Throughout the last year, organizations of all sizes and sectors have spent time familiarizing themselves with the csf 2.0 and many are in the process of upgrading their.
The free cybersecurity policy templates provided by this site can be downloaded as individual templates that are organized by the nist cybersecurity framework 2.0 core functions and. The templates can be customized and used as an outline of an organizational policy, w. Implementing policies closely aligned nist cybersecurity framework (csf) 2.0 enables organizations to adhere cybersecurity best practices in a flexible matter, which can be. Nist csf is widely recognized for helping businesses strengthen their security posture by following key nist csf controls. Nist cybersecurity framework policy template guide.
We are seeking your feedback on the publication’s contents and the future direction of nist’s ransomware guidance. Department of energy (doe) office of cybersecurity, energy security, and emergency. Resources include, but are not limited to: Nist csf is widely recognized for helping businesses strengthen their security posture by following key nist csf controls. Download free policy and standard templates for.
The national institute of standards technology (nist) cybersecurity framework provides a policy framework of computer security guidance for how private sector organizations can. Resources include, but are not limited to: The templates can be used as an outline of an organizational policy, w. Approaches, methodologies, implementation guides, mappings to the framework, case studies, educational materials,. The nist national cybersecurity center.
An access control policy defines how your organization manages user access to systems, data, and applications. The state of new york and the state of california. The nist national cybersecurity center of excellence (nccoe) and the u.s. Approaches, methodologies, implementation guides, mappings to the framework, case studies, educational materials,. 6 functions of nist csf 2.0 framework the nist csf framework.
This guide gives the correlation between 49 of the nist csf subcategories, and applicable policy and standard templates. An access control policy defines how your organization manages user access to systems, data, and applications. Department of energy (doe) office of cybersecurity, energy security, and emergency. The templates can be customized and used as an outline of an organizational policy, w..
The state of new york and the state of california. Use this template to simplify the process of developing a nist csf 2.0. The national institute of standards technology (nist) cybersecurity framework provides a policy framework of computer security guidance for how private sector organizations can. This guide gives the correlation between 49 of the nist csf subcategories, and applicable.
Nist Csf Policy Templates - The templates can be used as an outline of an organizational policy, w. The free cybersecurity policy templates provided by this site can be downloaded as individual templates that are organized by the nist cybersecurity framework 2.0 core functions and. Resources include, but are not limited to: This guide gives the correlation between 49 of the nist csf subcategories, and applicable policy and standard templates. The document outlines the five main functions within the nist csf. Complianceforge nist cybersecurity framework compliance documentation templates.
This guide gives the correlation between 49 of the nist csf subcategories, and applicable policy and standard templates. We are seeking your feedback on the publication’s contents and the future direction of nist’s ransomware guidance. Resources include, but are not limited to: Users can download 36 policy templates aligned with each nist csf 2.0 core function. The national institute of standards technology (nist) cybersecurity framework provides a policy framework of computer security guidance for how private sector organizations can.
Throughout The Last Year, Organizations Of All Sizes And Sectors Have Spent Time Familiarizing Themselves With The Csf 2.0 And Many Are In The Process Of Upgrading Their.
The nist national cybersecurity center of excellence (nccoe) and the u.s. The free cybersecurity policy templates provided by this site can be downloaded as individual templates that are organized by the nist cybersecurity framework 2.0 core functions and. Nist cybersecurity framework policy template guide. Create your presentations about cybersecurity, threats, and their prevention using our 100% editable nist cyber security framework powerpoint template.
Csf 1.1 Archive Expand Or Collapse.
And technology cybersecurity framework (nist. This guide gives the correlation between 49 of the nist csf subcategories, and applicable policy and standard templates. Users can download 36 policy templates aligned with each nist csf 2.0 core function. The document outlines the five main functions within the nist csf.
View The Quick Start Guides.
Nist is the abbreviation of. Framework version 1.1 (pdf) framework version 1.1 core (excel) translations; To fill out this document, start by reviewing the policy templates provided. This guide gives the correlation between 49 of the nist csf subcategories, and applicable policy and standard templates.
The Templates Can Be Used As An Outline Of An Organizational Policy, W.
An access control policy defines how your organization manages user access to systems, data, and applications. Nist ir 8374 reflects changes made to the. For industry, government, and organizations to reduce cybersecurity risks. The state of new york and the state of california.